
Spear Phishing Attacks? Tactics, examples, and techniques
Keeping your small to midsized organization cyber secure is getting more challenging every year. And the hackers are no longer

Keeping your small to midsized organization cyber secure is getting more challenging every year. And the hackers are no longer
Small to mid-sized organizations are now one of cyber-criminals biggest targets. Now, over half of all attacks are directed at

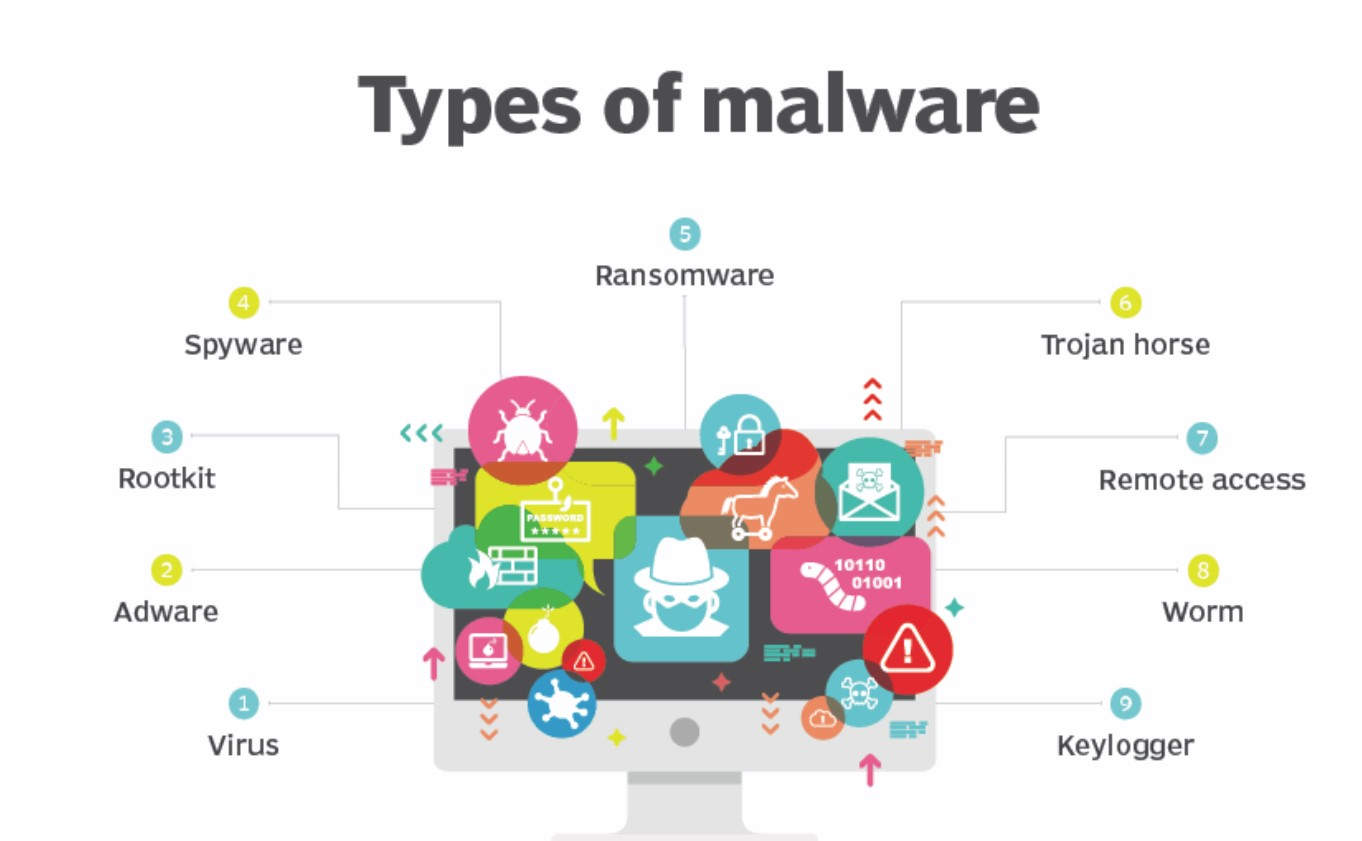
As cybersecurity software evolves worldwide, so do the tricks and techniques used to carry out cyber-attacks. Malware can easily cause

From phishing to brute force attacks, we’ll share with you the most common password attacks you’ll face One of the
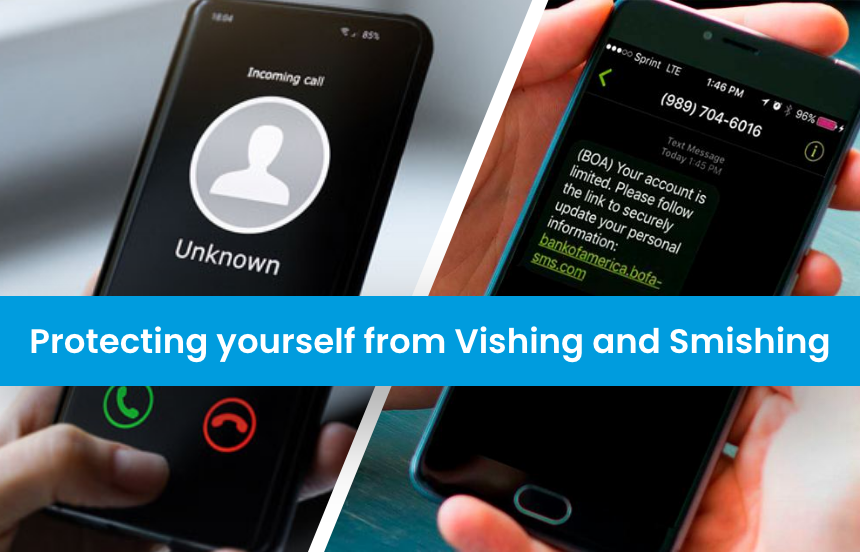
Phishing attacks are one of the most effective ways to breach your company. And they are evolving, changing, and growing

Cybersecurity alert: Roe Vs. Wade In a very emotional and far-reaching decision, the U.S. Supreme Court officially reversed Roe vs. Wade.

Nobody enjoys passwords. They are inconvenient for all of us. Interestingly, some companies and specific products and services are moving
As you can imagine, It’s pretty difficult to create a list of the top 10 technologies that have changed the

Amid the Russian invasion of Ukraine, and as the Russian military escalates its attacks, the United States is bracing for

Gilmore Solutions, a Managed IT Service Provider in Sterling, Kansas, announced it has merged with Imagine IT, a Cyber Security,
Our hearts are with the people of Ukraine and the innocent Russian people who do not support the senseless violence

The metaverse is coming, and it’s coming to Microsoft 365. Mesh is a platform that allows users to interact in

Whether calling Imagine IT, Comcast, or any other Tech Company We all know that feeling. You’ve got a tech issue,

No matter what you call it, the “Big Reshuffle, “The Great Resignation,” or “The Great Reset,” it’s clear that organizations

All organizations and their people are figuring out how to live with this new digital-first world, which was accelerated by

Employee burnout is happening more often in today’s business climate more than ever before. Why? Two main reasons. 2) A

Zoom Fatigue How to make video meetings easier At the end of a long day of back-to-back Zoom calls,

The 6 Biggest Cybersecurity Threats for 2022 There was an alarming increase in cyber security threats and breaches in

7 biggest challenges and realities of a hybrid office written by Marc Miller (Co-Founder of Imagine IT) There are legitimate

As one of the first Managed Service Providers in the Twin Cities, it’s not surprising that cool tech gadgets would

Working from home or remotely is here … and it’s here to stay! Since the pandemic, working from home or

How to position your business to thrive in the new hybrid world You are invited … When:

Hello, world – seeking fabulous team members! Does this ring true for you, like it does for us here at

It probably won’t surprise you that people average over 5 hours a day responding to emails. According to Adobe, Americans

Our Co-Founder and Chief Security Officer at Imagine IT, Peter Durand has created The State of Cyber Security for the

Imagine IT is collecting new/gently-used hats, mittens and scarves on behalf of a wonderful local non-profit organization Hats & Mittens! We

Cyber Security begins in the Boardroom with the leaders of a business. It no longer can be the sole responsibility

… And why most businesses remain vulnerable Cyber criminals are more advanced today than they ever have been, causing

IT Strategy and Digital Transformation for CEOs and Leaders Creating an IT and technology strategy can feel

When you think of culture and digital transformation (Dx), what is the first thing that comes to mind? Other than
MAIN OFFICE

© 2024 Imagine IT Website by eMod, LLC