
What are The Top Three Trends in the Cybersecurity Industry?
The key question for many professionals is: Is cybersecurity a growing industry? The cybersecurity industry is changing at a very

The key question for many professionals is: Is cybersecurity a growing industry? The cybersecurity industry is changing at a very
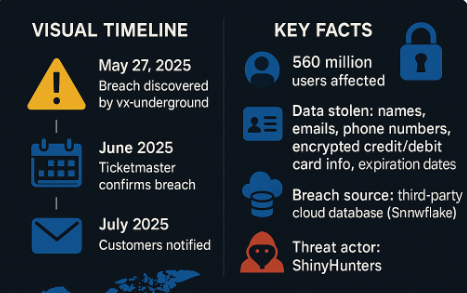
In 2024, the Ticketmaster Data Breach sent shockwaves through the cybersecurity world. As one of the largest ticket sales platforms,

10 MIN READ A distributed denial of service (DDoS) assault might bring your company to a complete halt, resulting in

10 MIN READ If you’ve ever wondered how hackers trick users into visiting fake websites, steal sensitive data, or cause

10 MIN READ Having strong IT assistance is essential in a time when technology influences every aspect of business operations.

10 MIN READ In today’s fast-paced digital landscape, you need to keep your IT costs in check if you want

10 MIN READ In 2024, the cyber threats financial services face are growing in complexity, making cybersecurity essential to protect

10 MIN READ The tech landscape in today’s world is highly competitive, and because of this, aspiring businesses are looking

10 MIN READ Data encryption is the cornerstone of business security. It protects critical information from unauthorized access and cyber

10 MIN READ Choosing the right IT support provider is essential for maintaining operational stability, ensuring cybersecurity, and enabling growth.

10 MIN READ Cloud-managed services have become essential for businesses aiming to optimize cloud performance, enhance security, and control IT

10 MIN READ The legal space is fast-paced, and new technologies, including artificial intelligence, are constantly being introduced. As a

10 MIN READ Technology is the core of every successful business. Because of this, many companies rely on tech solutions.

10 MIN READ Upgrading your business software is an important decision that impacts the efficiency, growth, and competitive edge of

10 MIN READ In this digital age, data loss can easily cripple a business. Small businesses, in particular, are prone

10 MIN READ It is crucial to take a step back often and look at the business operations more closely.

10 MIN READ Cyber risk management is a crucial component of the wider efforts of an organization to manage risks.

10 MIN READ On July 19, 2024, CrowdStrike, a US-based cybersecurity organization, released a faulty update to its security software.

10 MIN READ Cloud computing has become the basis of modern IT strategies. Gartner predicts that it will evolve to
10 MIN READ TLDR The technological singularity is a hypothetical point where AI surpasses human intelligence and begins improving itself.

10 MIN READ Data breaches continue to be a common threat to individuals, businesses, and organizations alike. While some industries,

10 MIN READ The manufacturing and distribution industry relies heavily on powerful IT infrastructures to stay in competition and increase

10 MIN READ In today’s tech-savvy world, businesses utilize data analytics, but many lack access to business intelligence (BI) technologies
10 MIN READ Every business owner is looking for opportunities to explore different services, and your business’s growth and success

10 MIN READ Safeguarding sensitive patient information is essential in the healthcare industry. Cybercriminals increasingly target healthcare providers through phishing

10 MIN READ Organizations need connectivity more than ever, partly because many crucial company processes are now carried out online.

10 MIN READ As many as 5,887 healthcare data breaches of over 500 records were reported to the Office for

10 MIN READ Security Information and Event Management (SIEM) has become a critical component in modern cybersecurity frameworks. Today, organizations

10 MIN READ Businesses are facing a growing demand for more efficient and secure IT infrastructure. This has made managing

10 MIN READ IT Managed Services Agreements (MSAs) are essential in modern business partnerships. They offer a structured framework that