Prevent ransomware from taking over your device.
# Do not mistake ransomware for a virus.

Malvertising is a popular way for threat actors to distribute malware. It involves using online advertising to spread malware without requiring much user interaction. Even legitimate websites can direct users to criminal servers that collect information about their computers and select the most suitable malware to deliver, often ransomware.
Malvertising typically employs an infected iframe, an invisible element on a webpage that redirects users to an exploit landing page. Malicious code is then launched from the landing page via an exploit kit, all without the user’s knowledge, resulting in what’s known as a drive-by download.
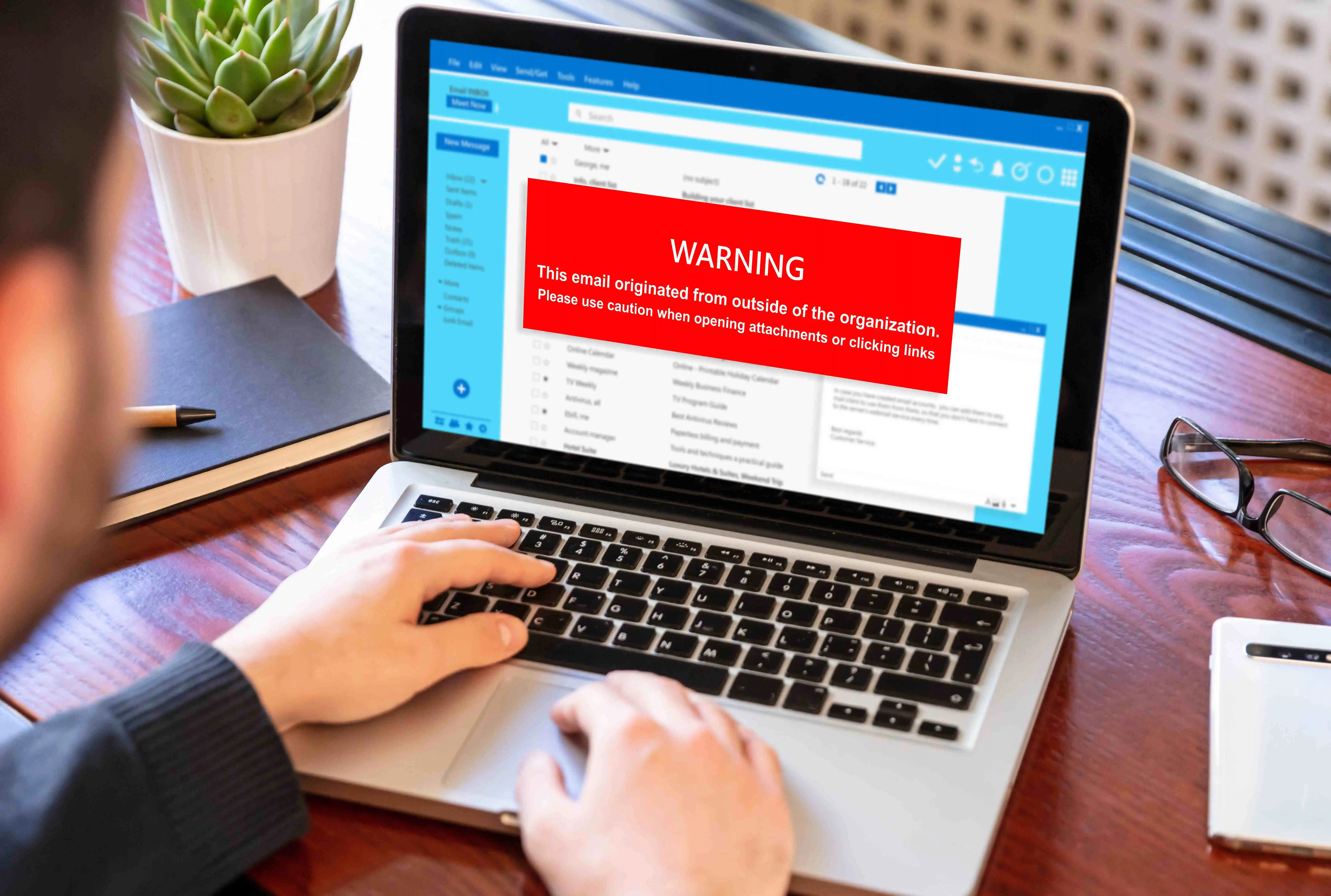
Spear phishing is a focused approach for conducting ransomware attacks. This method involves sending emails to specific individuals or groups, such as employees of a particular organization.
The attackers often use social engineering tactics, like sending an email that appears to be from the CEO, asking the recipient to take a critical survey, or downloading a new policy. In some cases, high-level decision-makers, such as executives, may be targeted using a technique called “whaling.”
Social engineering is a common tactic used in ransomware attacks, including malspam, malvertising, and spear phishing. Cybercriminals use social engineering techniques to deceive users into opening infected attachments or clicking on malicious links.
They may impersonate trusted institutions or people or gather personal information from social media to craft believable messages. In some cases, threat actors may even pose as law enforcement to intimidate victims into paying a ransom.
There are several types of ransomware attacks, but the three most common ones are:
Scareware isn’t as scary as it sounds. It’s usually made up of fake security software or tech support scams. You might get a pop-up message claiming that your device has malware and that paying up is the only way to remove it.
However, if you don’t do anything, you’ll keep seeing these pop-ups, but your files will be safe. Legitimate cybersecurity software would never ask for payment like this.
Detect, Eliminate & Block Ransomware with Imagine IT Today!


Irrespective of the various kinds of ransomware, they typically adhere to the subsequent procedure.
Here are the steps involved in a typical ransomware attack:
WannaCry: was a potent ransomware worm that exploited a Microsoft vulnerability, infecting over 250,000 systems worldwide. A killswitch was triggered to halt its spread. Proofpoint played a role in locating the sample used to find the killswitch and in analyzing the ransomware.
CryptoLocker was among the first ransomware to demand payment in cryptocurrency (Bitcoin) and encrypt a user’s hard drive and attached network drives.
It was distributed through an email attachment posing as FedEx and UPS tracking notifications. A decryption tool became available in 2014, but it is estimated that CryptoLocker extorted over $27 million from victims.
NotPetya is one of the most destructive attacks based on the Petya ransomware. It encrypts the master boot record of a Windows-based system and spreads rapidly via the same WannaCry vulnerability.
Victims were asked to pay in Bitcoin to undo the changes, but some considered it a “wiper” since it cannot reverse the damage and renders the system unrecoverable.
Bad Rabbit, similar to NotPetya, utilized comparable code and exploited it to spread. It was a prominent ransomware that appeared to target media companies in Russia and Ukraine. Unlike NotPetya, Bad Rabbit provided a decryption option if the ransom was paid.
REvil is created by a financially driven group of attackers who steal data before encrypting it. This allows them to blackmail their targets if they refuse to pay the ransom.
The attack was initiated by breaching IT management software to update Windows and Mac infrastructure. The attackers compromised Kaseya’s software, injecting REvil ransomware into corporate systems.
Ryuk is a ransomware application that is manually distributed, primarily through spear-phishing. The attackers perform a survey to select their targets carefully.
Once chosen, email messages are sent to the victims, and all files on the infected system are encrypted.
Ransomware attacks can target individuals, businesses of all sizes, non-profit organizations, and even government agencies. Essentially, anyone who uses computers and the internet can be a target for ransomware attacks.
However, some high-risk groups include healthcare organizations, financial institutions, and government agencies because they deal with sensitive information and are more likely to pay a ransom to retrieve access to their data.


With an experience of over 25 years, we specialize in supporting small to mid-sized organizations across diverse industries, offering tailored IT support and comprehensive cybersecurity solutions that meet each organization’s unique needs.


We provide top-tier cybersecurity solutions at Imagine IT to prevent such attacks. Our powerful internet security software suite can help you identify vulnerabilities and counteract malicious attacks, thereby minimizing the risk of a potential data breach.
Take the first step by speaking with our cybersecurity experts today and safeguarding your organization’s critical assets against ransomware attacks!

© 2024 Imagine IT Website by eMod, LLC