Cybersecurity gaps: What to look for, look out for … and what questions to ask
The stakes have never been higher regarding securing your cities and counties’ infrastructure.
With cities and counties relying more on technology to function effectively, vulnerabilities in IT systems can spell disaster for public services.
This revealing article explores the top 8 cybersecurity gaps in city and county IT systems that City Administrators and Managers should be aware of.
These gaps, ranging from obsolete software to insufficient staff training, present substantial risks to the security and performance of your essential public services. Recognizing and addressing these weaknesses can build a more resilient digital landscape for our communities.
Pinpointing and evaluating these eight gaps within your city or county IT systems will empower you to strengthen the security of your operations. Moreover, it will enable you to pose the most relevant cybersecurity questions to your IT team or provider, ensuring a robust defense against potential threats.
The Top 7 Cybersecurity Gaps for Cities and Counties
1. Outdated Software
 Software and firmware updates are easy to overlook, but they’re the unsung heroes of cybersecurity. These updates often come with critical patches to address security flaws, ensuring your systems are fortified against new threats.
Software and firmware updates are easy to overlook, but they’re the unsung heroes of cybersecurity. These updates often come with critical patches to address security flaws, ensuring your systems are fortified against new threats.
The Hidden Dangers of Outdated Systems
Running on outdated software and firmware is like leaving your front door unlocked. Hackers are always searching for new vulnerabilities, and older systems are ripe for exploitation. Therefore, local governments must stay vigilant and prioritize regular updates to prevent cyber-attacks.
Proactive Patch Management
Combat this vulnerability by establishing a comprehensive patch management strategy. Schedule regular updates and keep a close eye on software vendors’ announcements. By staying ahead of the curve, you’ll keep your city’s digital infrastructure secure.
2. Insecure Remote Access: When Convenience Becomes a Liability
 As remote work becomes more prevalent, ensuring secure access is crucial for local governments. Inadequate security measures can expose your systems to unauthorized access and data breaches.
As remote work becomes more prevalent, ensuring secure access is crucial for local governments. Inadequate security measures can expose your systems to unauthorized access and data breaches.
Balancing Remote Work and Security
While remote access offers flexibility and convenience, it can also create security gaps. Consider implementing multi-factor authentication, VPNs, and access controls based on user roles to strike the right balance.
Remote Access Policy Best Practices
Develop a robust remote access policy that outlines acceptable use, required security measures, and user responsibilities. By clearly communicating expectations, you can minimize the risks associated with remote work.
3. Weak Password Policies: The Gateway to Cyber Attacks
 A strong password is the first line of defense against cyber threats. However, many users still rely on weak, easily-guessable passwords, leaving systems vulnerable to attacks.
A strong password is the first line of defense against cyber threats. However, many users still rely on weak, easily-guessable passwords, leaving systems vulnerable to attacks.
Encouraging Strong Passwords
Educate employees on the importance of secure passwords and provide guidelines for creating them. Implement password management tools to help users store and generate strong passwords.
Embracing Multi-Factor Authentication
Add an extra layer of security by using multi-factor authentication (MFA). MFA requires users to provide additional verification, such as a fingerprint or a unique code sent to their mobile device, ensuring only authorized users gain access.
4. Inadequate Incident Response Plan
 When a cyber-attack occurs, time is of the essence. An effective incident response plan ensures your team can quickly identify, contain, and remediate threats, minimizing potential damage.
When a cyber-attack occurs, time is of the essence. An effective incident response plan ensures your team can quickly identify, contain, and remediate threats, minimizing potential damage.
The Importance of a Well-Defined Plan
A comprehensive incident response plan should outline roles, responsibilities, communication protocols, and procedures for handling incidents. This plan will serve as a roadmap, guiding your team through the chaos of a cyber attack.
Regularly Review and Update Your Plan
As threats evolve and your organization changes, so should your incident response plan. Regularly review and update your plan, incorporating lessons from previous incidents and emerging best practices.
5. Poorly Configured Firewalls & Intrusion Prevention Systems
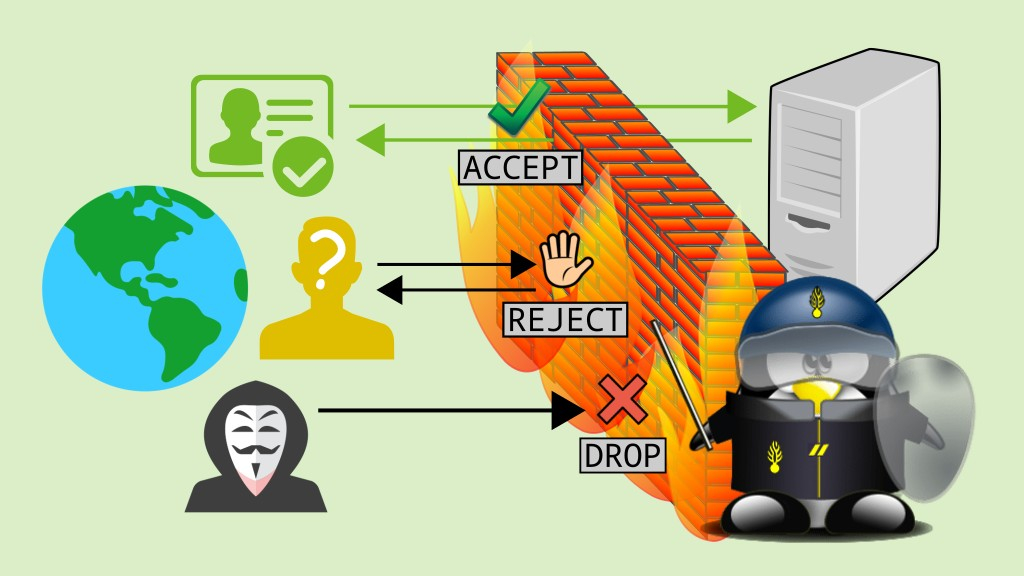 Firewalls and intrusion prevention systems (IPS) are vital gatekeepers, monitoring incoming and outgoing traffic for signs of malicious activity. However, if not properly configured, these guardians can be rendered ineffective.
Firewalls and intrusion prevention systems (IPS) are vital gatekeepers, monitoring incoming and outgoing traffic for signs of malicious activity. However, if not properly configured, these guardians can be rendered ineffective.
Optimizing Your Defenses
Regularly review and update firewall rules and IPS policies to ensure they align with your city’s security needs. Implement rule-based access controls and monitor logs to identify and address potential security issues.
Staying Informed on Emerging Threats
As new threats emerge, updating your firewalls and IPS to recognize them is crucial. In addition, subscribe to threat intelligence feeds and collaborate with other local governments to stay informed on the latest cyber risks.
6. Unauthorized Physical Access: When the Enemy is Inside the Gates
 Despite advances in digital security, physical access to critical systems remains a significant risk. Unauthorized access can lead to data theft, system damage, or even the introduction of malware.
Despite advances in digital security, physical access to critical systems remains a significant risk. Unauthorized access can lead to data theft, system damage, or even the introduction of malware.
Implementing Strong Access Controls
Establish access controls based on the principle of least privilege, granting employees access only to the systems and data necessary for their job. Use a combination of card readers, biometric scanners, and security cameras to monitor and restrict access to sensitive areas.
Educating Employees on Physical Security
Regularly train employees on the importance of physical security, including the risks of tailgating and the proper procedures for reporting suspicious activity.
7. Inadequate Employee Cybersecurity Training: The Human Element
 Even the most advanced security measures can only be useful if employees are trained to recognize and respond to cyber threats. A well-informed workforce is your city’s best defense against cyber-attacks.
Even the most advanced security measures can only be useful if employees are trained to recognize and respond to cyber threats. A well-informed workforce is your city’s best defense against cyber-attacks.
Building a Culture of Security
Develop a comprehensive cybersecurity training program covering phishing, social engineering, and password best practices. Make this training mandatory for all employees, with regular refreshers to keep knowledge up-to-date.
Encouraging Employee Vigilance
Promote a security culture by encouraging employees to report potential threats and rewarding those with exceptional cybersecurity awareness. In addition, you can empower your team to protect your city’s digital infrastructure by fostering a sense of shared responsibility.
Conclusion
As city and county administrators and managers, you are faced with many responsibilities, and cybersecurity is an essential aspect that requires your attention. This article aims to provide a clear and concise overview of the pressing issues affecting local governments’ digital infrastructure, along with actionable solutions to tackle them effectively.
Staying current with the latest technologies is vital for any city that wishes to remain competitive in today’s rapidly evolving digital landscape. You can achieve increased efficiency, accuracy, and cost savings by addressing these vulnerabilities proactively.
The journey towards a more secure future starts with taking action. So don’t wait for threats to become crises. Instead, consider contacting Imagine IT for valuable insights and schedule a demo to explore the next generation of Managed Service Providers tailored to your city’s unique needs.
In conclusion, local governments must embrace cutting-edge technology and remain vigilant against ever-evolving cyber threats.
By being proactive and investing in the right solutions, cities can safeguard their digital assets and ensure their communities’ well-being and prosperity.





