TL;DR
Endpoint security is a solution that protects a particular network within an organisation and prevents cyberattack threats across multiple devices. It is expert-led protection across endpoints, clouds, and digital assets.
- 24/7 real-time monitoring and instant incident response
- Advanced security tools and expertise access
- Affordable costs compared to other security solutions
- Compliance and reduced risk exposure
- Outgrown protection that scales with the business
- Quick threat detection
The Remote Work Era and the Rise of Endpoint Security
Picture this: It’s 9 a.m., and instead of sitting at your office desk, you’re logging in from a café, your living room, or even by the beach. In the post-COVID era, hybrid and remote work have become the standard for many companies.
However, with this flexibility comes a growing challenge. Employees working outside traditional office environments are vulnerable to cyberattacks, regardless of the device they use. For attackers, it is an opportunity. For businesses, it is a serious risk.
The frontline defense against these threats is endpoint security. It acts as a shield that protects every device connected to your company’s network, no matter where work happens.
In this blog, we’ll explain what endpoint security is, why it matters, and how you can use it to strengthen your defenses in a borderless workplace.
For Seamless Onboarding
What Is Endpoint Security in Cybersecurity?
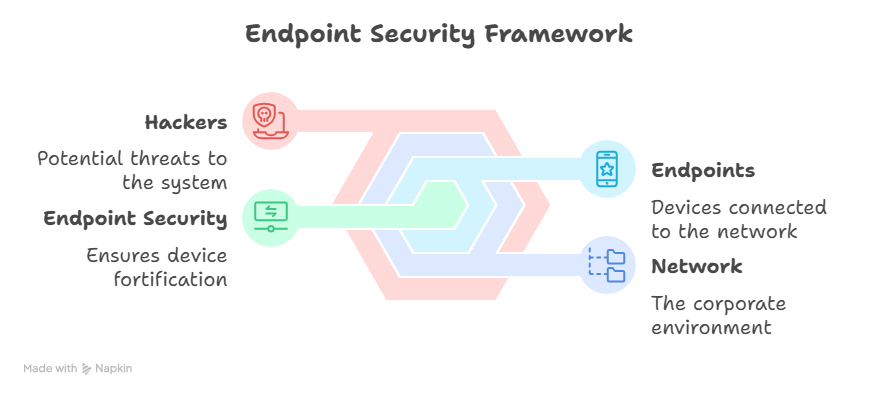
In simple terms, endpoint security refers to the protection of devices, commonly referred to as “endpoints,” that are connected to a specific network. An endpoint can be a laptop, smartphone, desktop, tablet, or even an IoT device, such as an innovative printer.
Each one represents and consists of a potential entry for attackers.
Endpoint security ensures that each device is fortified before it is introduced into the overall corporate environment. It has three main goals: Prevention, Detection, and Response.
Why Is Endpoint Security Essential for Remote Workers in 2025?
Remote work is a convenient way to work, and many companies have adopted the model. However, with widespread internet access, devices are more vulnerable to compromise. Remote workers are not privy to the security measures extended to in-office employees. Here’s what to consider:
- Employees often connect over public Wi-Fi.
- Devices may lack corporate-grade security tools.
- Sensitive company data is spread across countless endpoints.
For attackers, this decentralization is a dream come true. For businesses, it can be a nightmare.
Endpoint security software provides the visibility and control organizations need to secure every device, regardless of location. Without it, even one careless click on a phishing email could compromise an entire company.
Key Features of Effective Endpoint Security Solutions
Effective endpoint security in 2025 should include the following features:
- AI-driven threat detection: Easily catches and detects new incoming threats.
- Zero Trust architecture: No automatic tactics, only human form authentication for security issues.
- Data encryption: It helps ensure that stolen data is useless without the proper keys.
- Multi-factor authentication (MFA): An extra strong layer of security that acts as a shield.
- Automated patching and continuous monitoring: Devices are kept up to date with security-compliant implementations. Real-time alerts and consistent monitoring can help prevent attacks before they occur.
- Centralized management: Provides visibility to teams across all devices, regardless of network or location.
- Endpoint Detection and Response (EDR): Enables the rapid investigation and containment of threats. Set clear protocols to help recover the affected devices faster and isolate them quickly.
- Continuous Training: Regular and timely training, especially for new employees, can sensitive individuals and train them to look out for red flags.
Common Threats That Endpoint Security Helps Prevent
Here are the most pressing threats endpoint security defends against:
- Phishing attacks: Fake emails leading users to share essential credentials.
- Ransomware: Malicious code designed to extort money by holding critical data ‘hostage’.
- Data theft: Devices are attacked by hackers to steal sensitive customer information..
- Unauthorized access: Stolen passwords or weak authentication are exploited to gain unauthorized entry.
- Malware injections: Viruses, worms, and trojans hidden in downloads or attachments.
- Insider threats: Disgruntled or careless employees expose data intentionally or by mistake.
Each of these threats can cause financial losses, reputational damage, and even legal consequences. Strong endpoint security reduces the likelihood of these risks becoming costly disasters.

Challenges of Securing Remote Work Environments
While endpoint security is robust, businesses may face some challenges while implementing it:
- Device diversity: Employees use multiple devices, which can be both personal and office devices.
- Shadow IT: Employees can bypass IT controls when installing unauthorized apps and tools.
- Human error: The strongest system can’t stop someone from clicking an unsafe link.
- Scalability: Small businesses often lack resources for enterprise-grade security.
- Privacy concerns: Employees may deny security implementation due to personal reasons.
Conclusion
Remote work culture has become the new norm since the pandemic. While it offers ultimate freedom, it also brings increased cybersecurity risks.
Endpoint security protects businesses from the dangers of a careless click on a stolen laptop. With proper guidance and managed cybersecurity services, adapting endpoint security solutions is straightforward.
At Imagine IT, we go beyond traditional firewalls to deliver next-generation endpoint security solutions that shield every device connected to your network. With years of experience supporting Midwest businesses, we provide tailored cybersecurity strategies that prevent breaches, protect sensitive data, and ensure operational resilience.
For Seamless Onboarding
We deliver trusted cybersecurity solutions in Zeeland, Sterling, Bloomington, Wichita, and Garden City, helping local businesses stay secure against evolving threats. Partner with us today to strengthen your defenses, safeguard your operations, and stay prepared.
Corporate Headquarters: 952-905-3700
MN Technical Support: 952-224-2900
KS Technical Support: 620-278-3600 or Toll Free: 866-978-3600
MI Technical Support: 616-226-5546
Frequently Asked Questions
Q1. Why is endpoint security crucial for remote workers?
Ans. Endpoint security is essential for remote workers, as they are exposed to unsecured networks and other personal devices. It helps safeguard company data, ensuring secure access to business resources no matter where employees connect from.
Q2. How does endpoint security protect laptops and mobile devices?
Ans. Endpoint security protects all the devices that belong to a particular network. It utilizes firewalls, encryption, real-time monitoring, and automated responses to block threats as they are identified.
Q3. Can endpoint security prevent phishing and ransomware attacks?
Ans. Yes, endpoint security prevents phishing and ransomware attacks by identifying suspicious activity (such as accessing unknown links), blocking malicious files, and isolating infected devices to prevent the spread of ransomware attacks.
Q4. What risks do companies face without endpoint security?
Ans. Companies face various risks when they are not secure with endpoint security, including data breaches, ransomware attacks, financial fraud, compliance violations, and reputational damage to the organisation.
Q5. How can businesses use remote work security without affecting productivity?
Ans. Remote work security can be enhanced through the use of cloud-based endpoint security, automated updates, the installation of MFA, and employee training. Organizations can ensure adequate protection without disrupting overall workflow.