How To Prevent Phishing attacks?
There has been a lot of press about cybersecurity breaches over the past couple of years. And the Pandemic has made things that much easier for hackers as emotions run high.
Cyber security is a real and serious concern for small to mid-sized organizations, and that concern is well-founded and something you can’t take lightly.
But, there is one big misunderstanding regarding cyber security breaches
For example, we have one of the most robust and fully layered cyber security solutions for small to mid-sized businesses at Imagine IT.
So the problem for our client-partners and you isn’t a lack of firewalls, intrusion detection systems, VPNs, encryption, or other cyber security technology.
The biggest cause of breaches and successful prevent phishing attacks are humans.
No matter how sophisticated, sneaky, or technically advanced the bad guys are, they are still constrained and thwarted by current cyber security measures.
And even though these cybercriminals would love to embed malware onto your network, one of your people needs to let them in. You can learn more about the different types of malware and ways to combat them by clicking here.
One of your employees needs to click on a malicious link for phishing to work
To help, we have identified 7 ways your organization can prevent phishing attacks, saving your company millions of dollars and the embarrassment of your clients’ and customers’ personal data being exposed.
7 ways to Prevent Phishing Attacks

-
Know what a phishing scam looks like
The latest phishing attack methods are being developed all the time. However, they share commonalities you can only identify if you know what to look for. Many online sites help inform people of the new phishing attacks and their key identifiers. The earlier you discover the latest attack methods, the more likely you will avoid a potential attack.
Phishing emails and text messages will look like they’re from a company you trust, like your bank, insurance agent, or even your credit card company. Social media sites are also a favorite for phishing scams.
Phishing emails often include a story trickling you into clicking a link or even a malicious attachment.
These emails may say
- They’ve noticed suspicious activity on your account.
- There is a problem with your account
- Offer free stuff
- Include a fake and malicious invoice
- Ask you to confirm some personal information
- You are eligible for a refund
- Please update your payment details
-
Watch out for shortened links
Attackers can easily use shortened links to trick you into clicking and don’t even show a website’s real name. Hackers use shortened links to redirect recipients to fake look-alike sites and capture their sensitive information. Before clicking on the shortened link, always place your cursor on it to see the target location.
-
Don’t provide your personal information in response to an unsolicited request

Never mistake providing your personal information in response to an unsolicited request, whether over the internet or the phone. Phishers create emails and Internet pages that can look exactly like the real thing, and they may also use a fake padlock icon that ordinarily denotes a secure site. Therefore, you should not provide any information if you did not initiate the communication.
-
Be Wary of Pop-Ups

Pop-up windows usually masquerade as a website’s legal components, and often, all are phishing attack attempts. Use one of many famous browsers that allow people to block pop-ups. And if need be, you can even allow them case-by-case basis. If you slip through the cracks, don’t click the “cancel” button because such buttons can lead to phishing sites. Instead, click the small “x” in the upper corner of the window to avoid phishing attacks.
-
Get free anti-phishing add-ons

Nowadays, most browsers enable you to download add-ons that alert you about known phishing sites or spot the signs of a malicious website. Usually, they are completely free; therefore, install them on every device you own if you haven’t already.
-
Use Firewalls
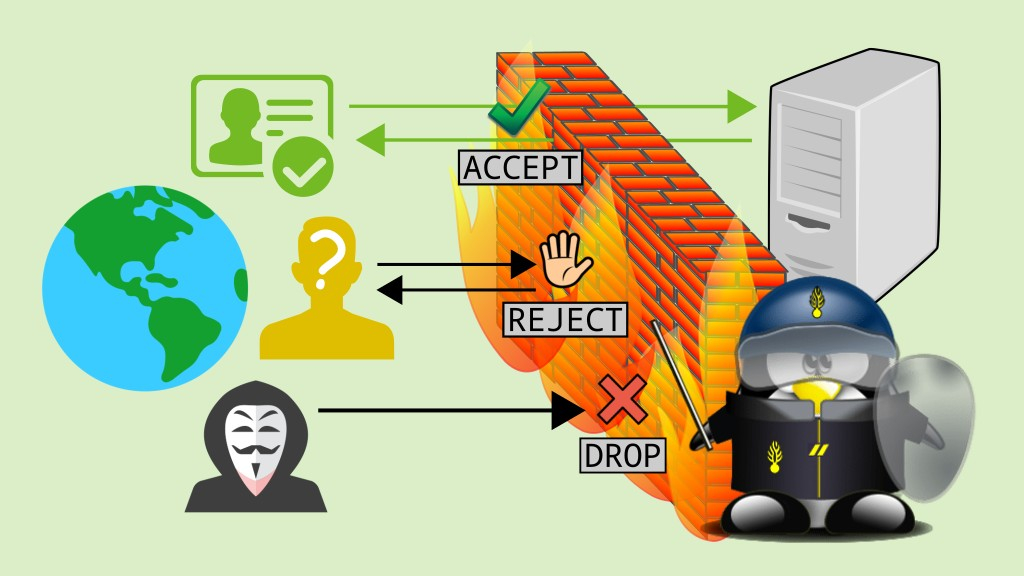
High-quality firewalls act like buffers between you, your computer, and outside intruders. You should use two different kinds: a network firewall (a type of hardware option) & a desktop firewall- (a type of software option). When used together, these firewalls drastically reduce the odds of hackers and phishers infiltrating the computer and your network.
-
Bad grammar and punctuation
Professional copywriters go to great lengths to create emails with the subject line, well-tested content, call-to-action, and more. Any email with poor punctuation, grammar, or likely illogical flow of content is likely written by inexperienced scammers and is fraudulent.
In Conclusion
Understanding the risks of phishing attacks and some of the most common ways cybercriminals will create emails to trick you is an important first step toward protecting you and your organization. Especially with so many of your people working remotely.
Although this list will help you better understand how phishing attacks work. Phishing campaigns are very sophisticated, and cyber-hackers are experts at pulling your heartstrings.
So there is a good chance one of your team members will fall prey to one eventually. So it is important to connect with a Managed IT service provider that offers a fully-layered cyber security solution.
Next Steps
If you would like to learn details about an enterprise-level, fully layered cyber solution created for small to mid-sized organizations, check out this link: The Security Shield
If you have more urgent needs and would like to discuss your current cyber security posture, have us perform a full free cyber security assessment. Please reach out to us today.






